Correlate Events to Send Syslog Alerts
The previous section showed syslog alerts between two hosts in a lab environment. In the real world, when thousands of an organization’s users access network resources, they can trigger a substantially higher volume of syslog messages. In this case, if you want to receive syslog messages only for an event that is generated during a very specific circumstance, you can leverage the functionality of the correlation policy to produce syslog events under the specific set of conditions you are interested in logging.
As the name suggests, a correlation policy enables the management center to correlate various datapoints and events that are received from threat defense devices. You can create correlation rules based on discovery events, intrusion events, file events, connection events, and a variety of other conditions. The management center can use correlation rule constraints to match an event generated under very specific circumstances. As a response to the rule match, you can instruct the management center to send alerts to a syslog server in your correlation policy configuration.
The following steps demonstrate how to create a correlation rule to match a specific malware event and then send a syslog alert as a response to a violation of that rule:
Step 1. Navigate to Policies > Correlation. Select the Rule Management tab. The rule management page appears (see Figure 21-20).
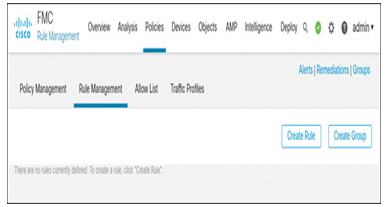
Figure 21-20 The Rule Management Tab Provides an Option to Create a New Correlation Rule
Step 2. Click the Create Rule button. The correlation rule editor page appears.
Step 3. Under the Rule Information tab, name the rule. Then, under the Select the Type of Event for This Rule section, you can use the drop-down to develop rule conditions. Use the Add Condition and Add Complex Condition buttons to define the rule logic, as necessary. When you are done, click the Save button to save the rule.
Figure 21-21 displays a correlation rule that detects the download of malicious files on two specific hosts. In a real-world scenario, they might be two important hosts: the chief executive officer (CEO) and chief financial officer (CFO) of a company.
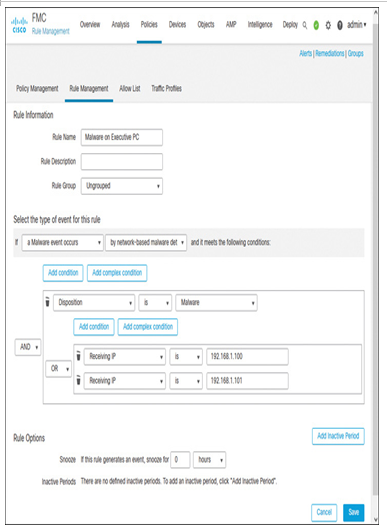
Figure 21-21 A Correlation Rule
Step 4. On the Policy Management tab, click the Create Policy button (see Figure 21-22).
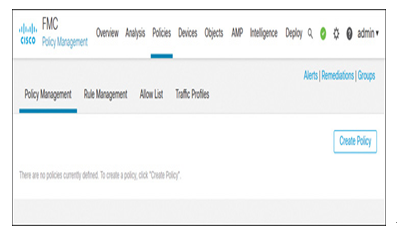
Figure 21-22 The Policy Management Tab Provides an Option to Create a New Correlation Policy
Step 5. Give a name to the correlation policy. Click the Add Rules button. It shows the available correlation rules in a window.
Step 6. On the Available Rule window, select the correlation rule you have just created and click the Add button (see Figure 21-23). The GUI returns to the Policy Management page. The correlation policy that you just created appears.
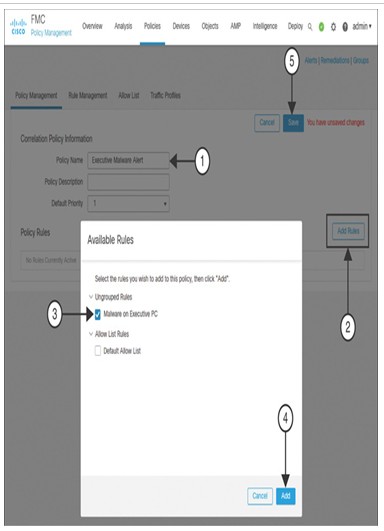
Figure 21-23 List of Available Correlation Rules
Step 7. Select the callout icon next to the policy name. When the response selection window appears, move the preconfigured syslog alert response to the Assigned Responses section, as shown in Figure 21-24.
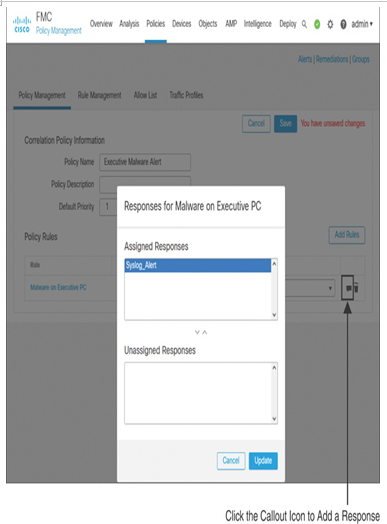
Figure 21-24 List of Available Responses
Step 8. Click the Update button. The GUI returns to the policy management window and displays the mapping of a correlation rule with a response, as shown in Figure 21-25.
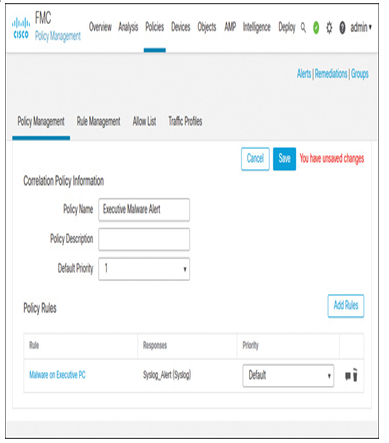
Figure 21-25 The Correlation Policy Shows the Mapping Between a Correlation Rule and a Response
Step 9. Click the Save button. After the policy is saved, make sure to activate it (see Figure 21-26).
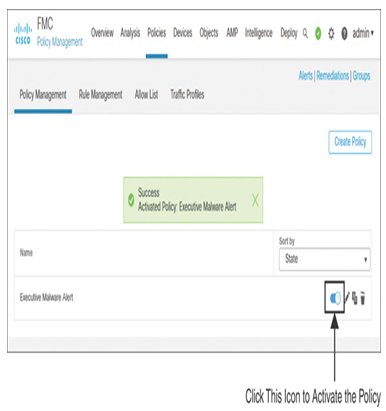
Figure 21-26 Activating a Correlation Policy