Troubleshooting Logs
In case of any technical issues with Secure Firewall, you can contact the Cisco technical assistance center. You may be requested to obtain troubleshooting files from your Secure Firewall and share the files with Cisco for advanced analysis. The troubleshooting files contain log messages of various processes, copies of configuration files, results of database queries, various command outputs, and so on. The files are critical to determine the root cause of any technical issues with Secure Firewall.
You can use the management center GUI to generate troubleshooting files from any threat defense devices as well as the management center. Following are steps to generate and download the files:
Step 1. On your management center GUI, open the System menu and navigate to Health > Monitor (see Figure 21-27). The health monitoring page appears.
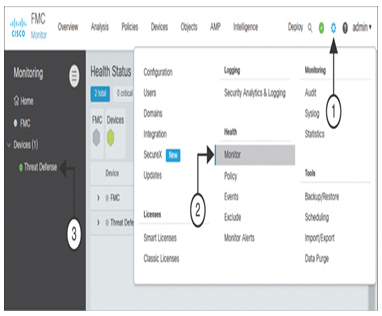
Figure 21-27 Navigating to the Health Monitoring Page
Step 2. On the left panel, you will find the management center and all the threat defense devices that are part of your Secure Firewall deployment. Select the device from which you want to generate the troubleshooting file.
Step 3. When the device-specific health status is displayed, select General Troubleshooting Files. The Troubleshooting Options window appears. Include all data, as shown in Figure 21-28.
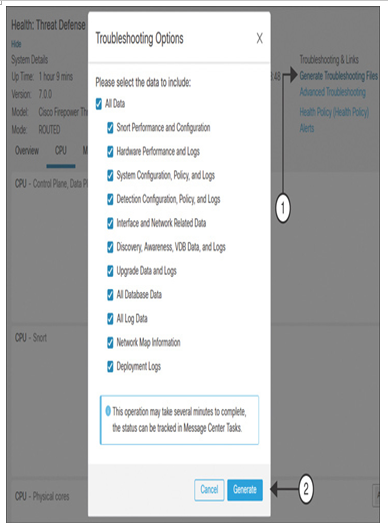
Figure 21-28 Selecting Troubleshooting Logs
Step 4. Click the Generate button to begin the troubleshooting file-generation process. After the file is generated, you can download it using the task status window (see Figure 21-29).
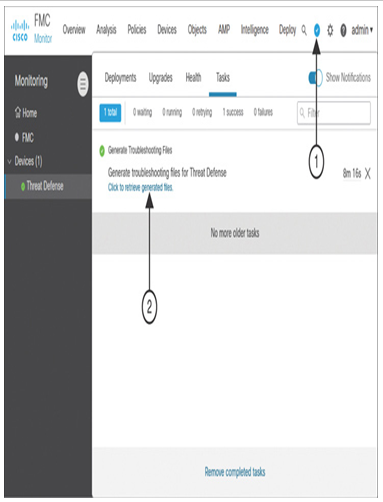
Figure 21-29 Link to Download Troubleshooting Files
If you simply want to view the syslog messages of the management center on the fly without generating the comprehensive troubleshooting files, you can click the System menu and navigate to Monitoring > Syslog, as shown in Figure 21-30.
Figure 21-30 Retrieving Syslog Messages on the Management Center GUI
Summary
This chapter demonstrates the generation of different types of security events and the ability to send corresponding syslog messages to an external syslog server. It delineates the procedures for sending syslog messages from the management center and threat defense devices using two different options: platform settings policy and alert responses. Finally, it describes the steps to create a correlation policy to issue syslog alerts in response to correlation policy rule violations.
As mentioned in the section “How to Use This Book” in the Introduction, you have a couple of choices for exam preparation: the exercises here, Chapter 22, “Final Preparation,” and the exam simulation questions in the Pearson Test Prep practice test software.
Review All Key Topics
Review the most important topics in this chapter, noted with the Key Topic icon in the outer margin of the page. Table 21-5 lists a reference of these key topics and the page numbers on which each is found.
Table 21-5 Key Topics for Chapter 21
| Key Topic Element | Description | Page |
| Paragraph | Choosing TCP or UDP for Syslog | 558 |
| Paragraph | Security level and facility | 559 |
| List | Syslog ports | 562 |
| Paragraph | Understanding correlation policy | 574 |